Ransomware
Overview
Ransomware is a huge global threat to businesses around the world. Businesses are projected to have paid out $20B in 2021, a 100% Y-o-Y increase for the last four years, and it’s only going to get worse with new business models like RaaS: ransomware-as-a-service. With Retrospect Backup, businesses can protect their infrastructure with immutable backups for ransomware protection.
Organizations need to detect ransomware as early as possible to stop the threat and remediate those resources. Anomaly Detection in Retrospect Backup identifies changes in an environment that warrants the attention of IT. Administrators can tailor anomaly detection to their business’s specific systems using customizable filtering and thresholds for each of their backup policies, and those anomalies are aggregated on Retrospect Management Console across the entire business’s Retrospect Backup instances or a partner’s client base with a notification area for responding to those anomalies.
The key to detection is combining technologies such as signature detection in processes with file-based irregularities for behavior-based monitoring. Using a multi-pronged defense, with immutable backups, anomaly detection, and other security layers, businesses will know when they’re being attacked and will have the tools to remediate it and move on. See Anomaly Detection for more details.
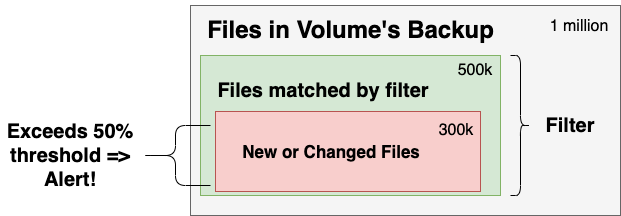
The diagram shows the volume being monitored as a whole, the subset of files that match the "Anomaly Detection" filter, and the files that are new or changed within that subset. Retrospect generates an alert if the percentage exceeds the threshold.
When an anomaly is detected, Retrospect can generate an email notification and surface the anomaly in the application and on Retrospect Management Console. It also provides API integration for businesses to tailor the workflow to their processes using Script Hooks.
Script Hooks
Retrospect administrators can use Retrospect’s external scripting to hook into Retrospect’s events. These hooks can be used to integrate with monitoring systems, quiesce databases and other services before a backup starts or alert the administrator to unusual error conditions. Script hooks can also be used as web hooks, triggering events on services such as Slack or IFTTT.
Retrospect triggers these events by calling a file named "RetroEventHandler". This file can be any script type known to the operating system (As examples for Windows, BAT or VBScript. For Mac, bash or ruby). They can even be compiled programs. For each event, Retrospect sends the name of the event followed by information specific for the event. Retrospect looks in the following locations:
- Retrospect for Windows: C:\ProgramData\Retrospect and C:\Program Files\Retrospect
- Retrospect for Mac: /Library/Application Support/Retrospect
- Retrospect Client for Windows: C:\Program Files\Retrospect\Retrospect Client
- Retrospect Client for Mac: /Library/Application Support/Retrospect Client/retroeventhandler
- Retrospect Client for Linux: /etc/retroeventhandler
Note that you do not need to restart the application for Retrospect to recognize the script hooks file. Also note that for Retrospect for Windows, script hooks are only supported for scripted executions, not immediate executions.
Retrospect has fifteen events that can be handled by scripts.
How to Stop a Backup
Let’s say an administrator did not want to continue a backup if an anomaly was detected. There are several good reasons for this path. If it’s ransomware, they don’t want to preserve the ransomware in their immutable backups or anywhere else in their backup infrastructure. If it’s not ransomware, they still don’t want to back up a significant increase in new or changed files without understanding why those files changed. The administrator wants the backup of any machine to stop if it detects an anomaly, given the filter and alert percentage that they set for that policy.
The administrator can use the AnomalyAlert script hook to know when an anomaly has been detected and then use the $interventionFile file within the launch script to stop the backup. See Script Hooks Examples for sample scripts.
With this simple process, the administrator can stop a backup as soon as an anomaly is detected, without preserving the suspect files.
How to Alert a Third-Party Service
Let’s say an administrator wants to integrate with a third-party alert service, like PagerDuty or Slack. The business might have their own IT system for tracking tickets and funneling Retrospect Backup anomalies into that system guarantees that the generated ticket will be examined and evaluated. Many organizations have systems like this set up to streamline and standardize the IT process for handling issues that come up. If Retrospect Backup detects an anomaly, IT would need the alert to show up in that system.
To do this, the administrator can use the AnomalyAlert script hook to find out when an anomaly has been detected and then integrate with the API of the third-party service in a Bash or shell script to generate the alert. See Script Hooks Examples for sample scripts.
Through a short script, the IT team can track and resolve detected anomalies in their standard system.
Last Update: February 15, 2022