VPN Backup
Optimized for remote employees on VPN that you want to protect with an on-site Retrospect Backup instance.
Retrospect Backup works seamlessly with VPNs. If your VPN supports multicast, Retrospect Backup will automatically discover and protect servers and endpoints that are connected over the VPN. If multicast is not supported, you can add servers, desktops, and laptops by their IP address. You can quickly onboard new remote employees using Automatic Onboarding on Retrospect Management Console.
Let’s walk through the steps with Automatic Onboarding on Retrospect Management Console.
Retrospect Backup for Windows: Onboard a new server or endpoint
In the backup server’s page, scroll down to see "Deploy Retrospect clients for endpoint protection". Note that servers are supported now as well.
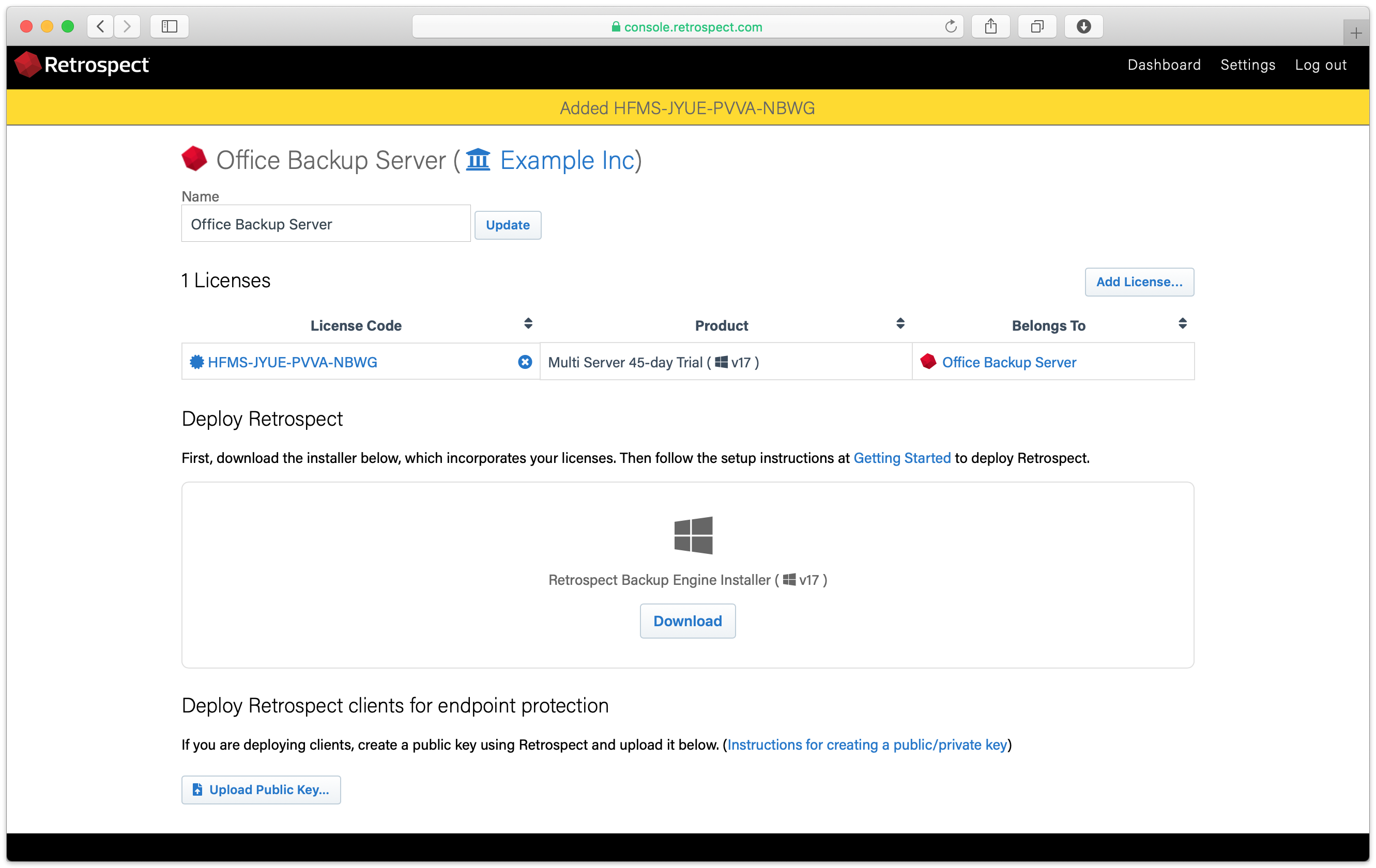
Upload the server’s public key. Retrospect Backup 17 enables you to automatically upload it to Retrospect Management Console. Simply go to Preferences. The public key file is located on the engine under /Library/Application Support/Retrospect/pubkey.dat on Mac and C:/ProgramData/Retrospect/pubkey.dat on Windows. Find it with "Upload Key" and then click "Upload".
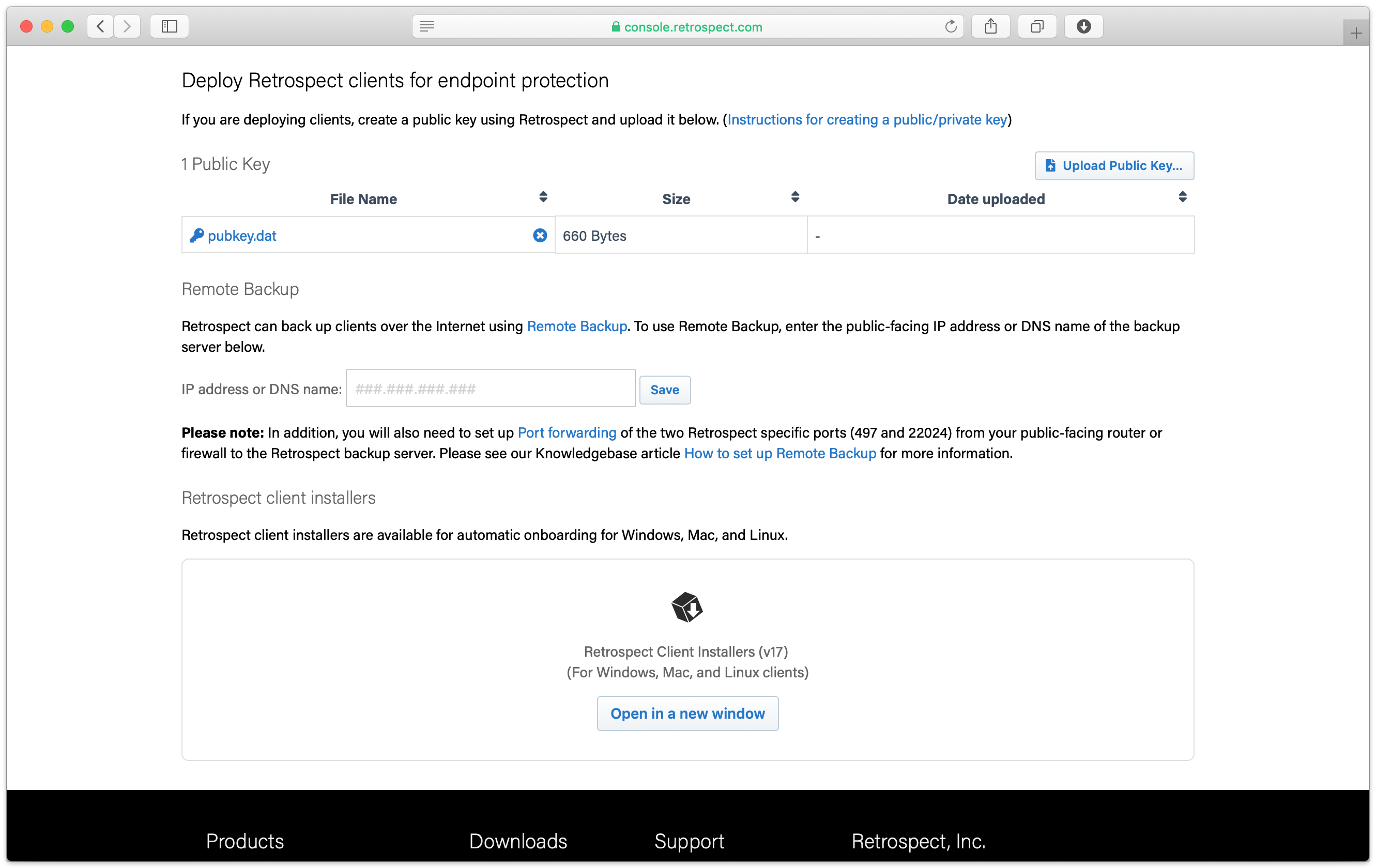
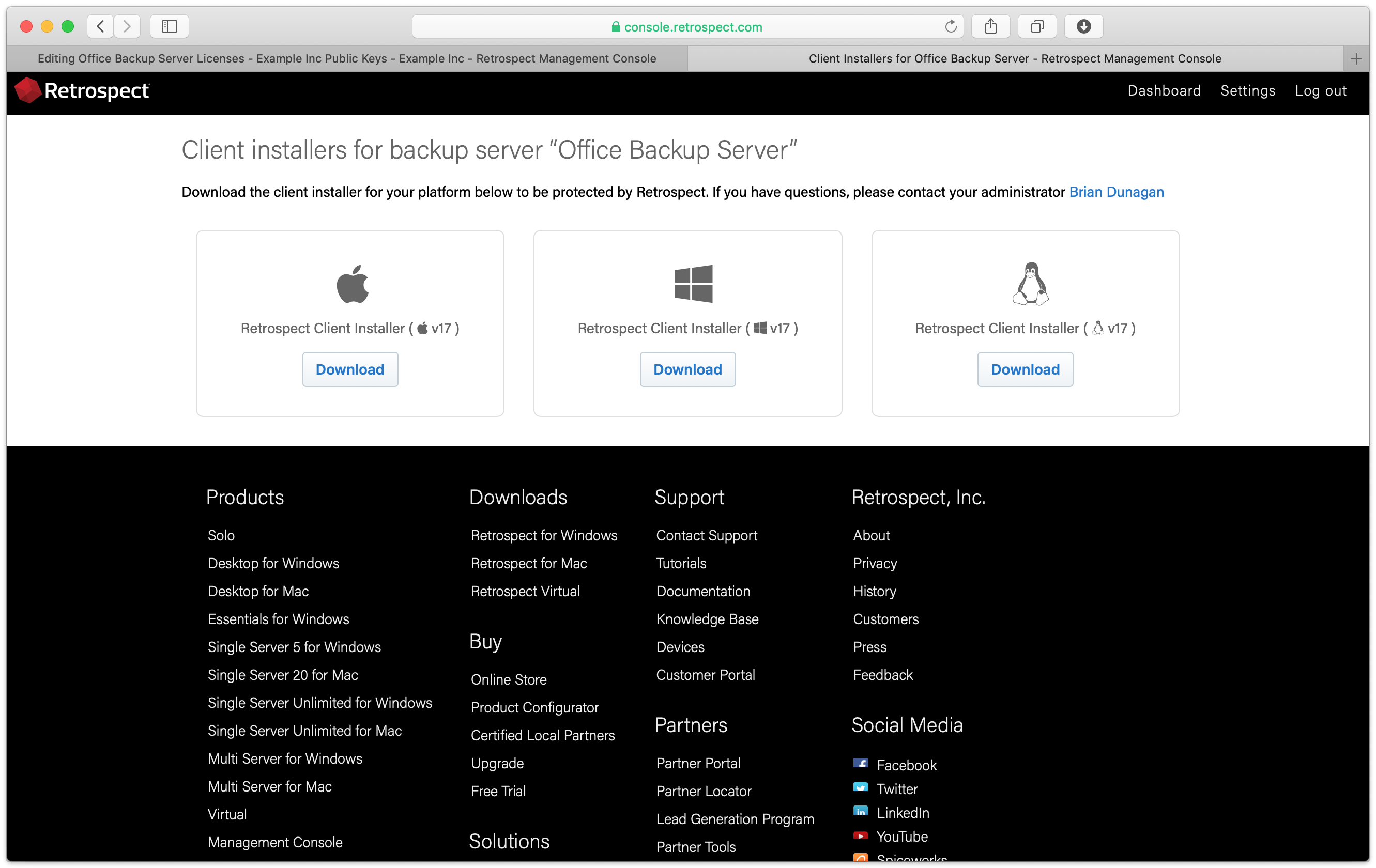
Under "Retrospect client installers", there is a link to share with end users. They can download the Retrospect Client for Windows, Retrospect Client for Mac, or Retrospect Client for Linux installers with the public key and remote backup address bundled in.
Your Retrospect Client agents are now set up to connect to your Retrospect Backup instance. Now we need to set up the Retrospect Backup instance to automatically add them and protect them.
Let’s walk through setting these up in Retrospect Backup without Retrospect Management Console.
Under Preferences > Clients, create a public/private keypair.
Locate the public key file.
Copy the public key file into the Retrospect Client installer’s "public_key" folder. You can download the Retrospect Client installer from
Compress the new installer and send it to your remote employee to install.
Now that the Retrospect Client agent can connect to the Retrospect Backup instance, let’s create a ProactiveAI backup script.
In Retrospect Backup, go to Preference then Clients and check "Automatically add clients using public keys".
Create a ProactiveAI script. This is under ProactiveAI on Windows and under Scripts on Mac.
Add a backup set as a destination. This can be either local storage or a cloud storage location.
Add "Automatically Added Clients" as the source. This is under Volumes on Windows and under Tags on Mac.
After you save, Remote Backup will be configured.
If you encounter any issues, please see further details in our User’s Guide:
Remote Backup
Optimized for remote employees outside of VPN that you want to protect with an on-site Retrospect Backup instance.
With Remote Backup, remote employee endpoints can be automatically added to a Retrospect Backup instance inside the corporate firewall and protected with a ProactiveAI script. There are no router changes needed on the employees side, and the IT administrator can make a simple change on the corporate firewall to forward inbound connections to Retrospect Backup. Remote employees are able to use on-demand restore to get files fast without assistance. Automatic Onboarding is a great way to deploy the Retrospect Client agent to your remote employees.
Remote Backup is designed specifically for endpoint protection and is not supported for server protection.
For Remote Backup to work, the Retrospect Client agent needs to be able to make a network connection the Retrospect Backup instance.
- Enable port forwarding for two ports to forward from the server-side public-facing IP on the router/NAT/firewall to the Retrospect engine.
- Set up the Retrospect engine to accept remote backups.
- Set up the Retrospect client to send periodic backup requests to the engine.
We’ll walk through each step.
Server-Side Network Configuration
Port Forwarding is a standard mechanism to redirect connections on a specific port from one IP to another. Retrospect Backup requires two ports:
- Port 497: multicast and remote backup broadcast
- Port 22024: on-demand requests
You need to set up your public-facing router/NAT/firewall to forward these ports to the IP address of the computer running your Retrospect Backup instance. With this networking change, a remote endpoint running the Retrospect Client agent will be able to make a connection to the Retrospect Backup instance, even though the computer running the Retrospect Backup instance is running on the internal network.
For guidance on enabling port forwarding, please refer to the hardware’s manual. The process varies by manufacturer.
You can verify that the ports are open using https://www.yougetsignal.com/tools/open-ports/. Remote backup will not work unless the ports are open.
Retrospect Backup Configuration
Retrospect Backup utilizes the following features for Remote Backup:
- Public/Private Keypair Authentication: This authentication automatically and securely identifies the remote endpoint as a trusted client without a password.
- ProactiveAI Backup: This backup script will automatically starts a backup for any remote endpoint that notifies the Retrospect Backup instance of its availability.
- On-Demand Restore: This restore workflow allows remote employees to restore files themselves without IT assistance.
Let’s walk through the steps with Automatic Onboarding on Retrospect Management Console.
In the backup server’s page, scroll down to see "Deploy Retrospect clients for endpoint protection".
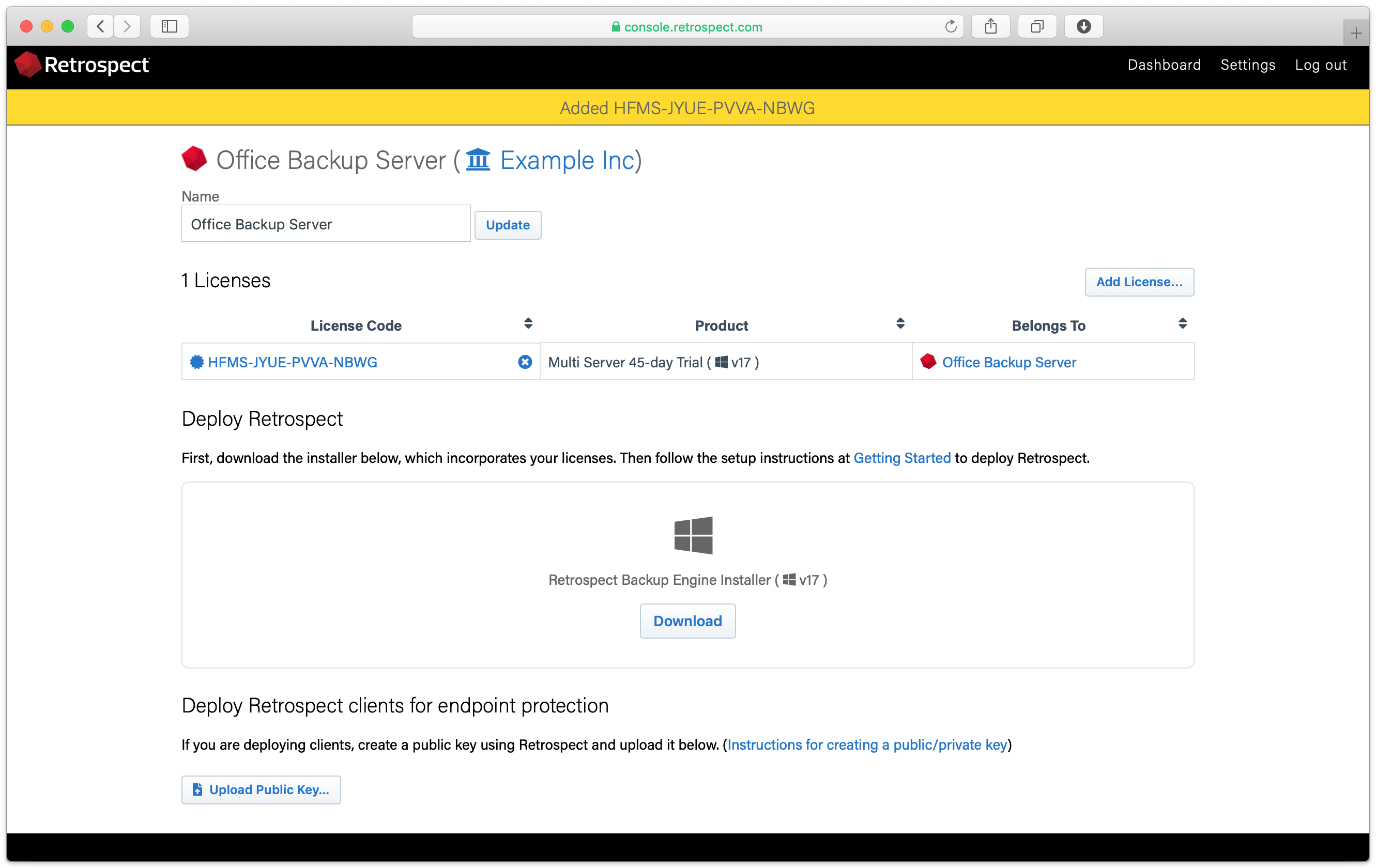
Upload the server’s public key. Retrospect Backup 17 enables you to automatically upload it to Retrospect Management Console. Simply go to Preferences. The public key file is located on the engine under /Library/Application Support/Retrospect/pubkey.dat on Mac and C:/ProgramData/Retrospect/pubkey.dat on Windows. Find it with "Upload Key" and then click "Upload".
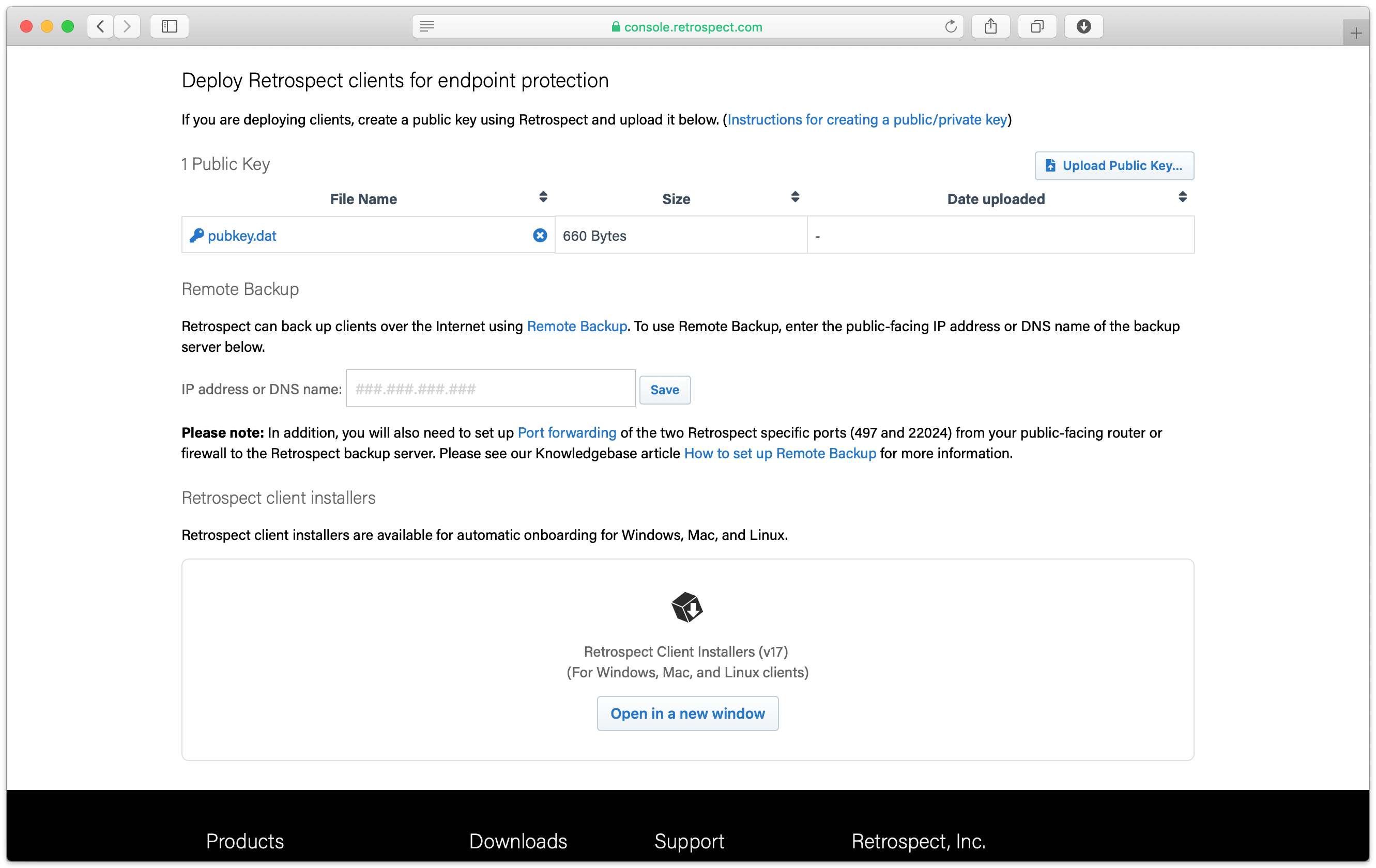
Enter the IP address or DNS name of the Retrospect Backup server under "Remote Backup", so that remote computers can connect to the port-forwarded public IP/DNS address.
Under "Retrospect client installers", there is a link to share with end users. They can download the Retrospect Client for Windows, Retrospect Client for Mac, or Retrospect Client for Linux installers with the public key and remote backup address bundled in.
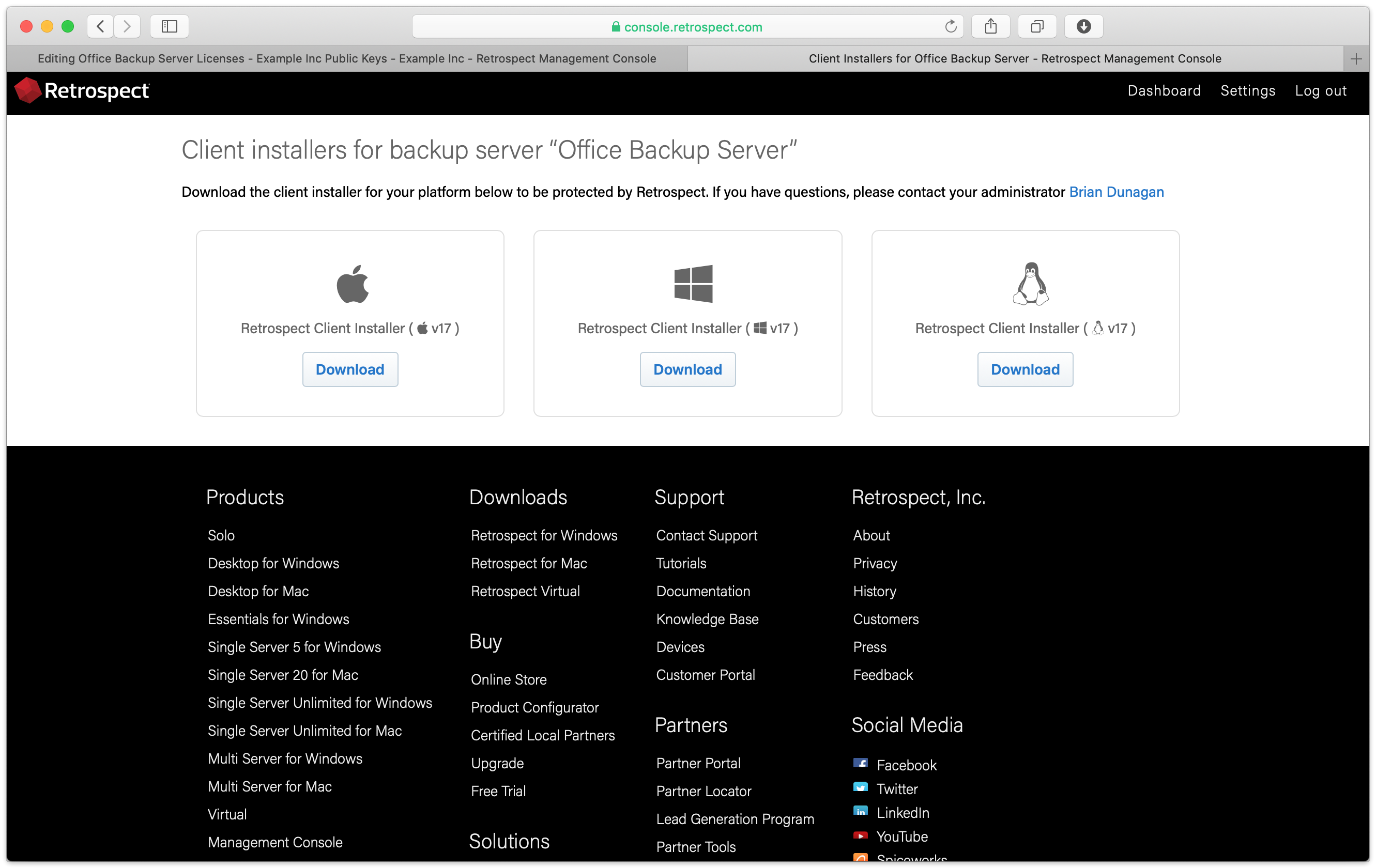
Let’s walk through setting these up in Retrospect Backup without Retrospect Management Console.
Under Preferences > Clients, create a public/private keypair.
Locate the public key file.
Copy the public key file into the Retrospect Client installer’s "public_key" folder. You can download the Retrospect Client installer from
Create a file called "server.txt" in the following location with the public DNS/IP address of the Retrospect Backup instance.
Compress the new installer and send it to your remote employee to install.
Now that the Retrospect Client agent can connect to the Retrospect Backup instance, let’s create a ProactiveAI backup script.
In Retrospect Backup, go to Preference then Clients and check "Automatically add clients using public keys".
Create a ProactiveAI script. This is under ProactiveAI on Windows and under Scripts on Mac.
Add a backup set as a destination. This can be either local storage or a cloud storage location.
Add "Remote Backup Clients" as the source. This is under Volumes on Windows and under Tags on Mac.
After you save, Remote Backup will be configured.
On-demand restore will automatically work using public key authentication.
If you encounter any issues, please see further details in our User’s Guide:
Cloud Backup
With Cloud Backup, remote employees can use Retrospect Backup to back up their corporate data to a cloud storage provider. Retrospect Management Console supports Automatic Onboarding to deliver a Retrospect Backup download and license to remote employees, and IT administrators can then configured a Shared Script on Retrospect Management Console to automatically deploy to those new instances. The endpoint will use the script to back itself up to a per-configured cloud storage location. Retrospect Backup Solo Premium is a great subscription license for this scenario, covers a computer and any connected device.
Let’s walk through setting up a new Retrospect Backup server and then using Shared Scripts to deploy a cloud backup sript to it.
Automatic Onboarding
Under Settings > Organizations, you will see our new Onboarding Assistant. Click "Onboarding Assistant".
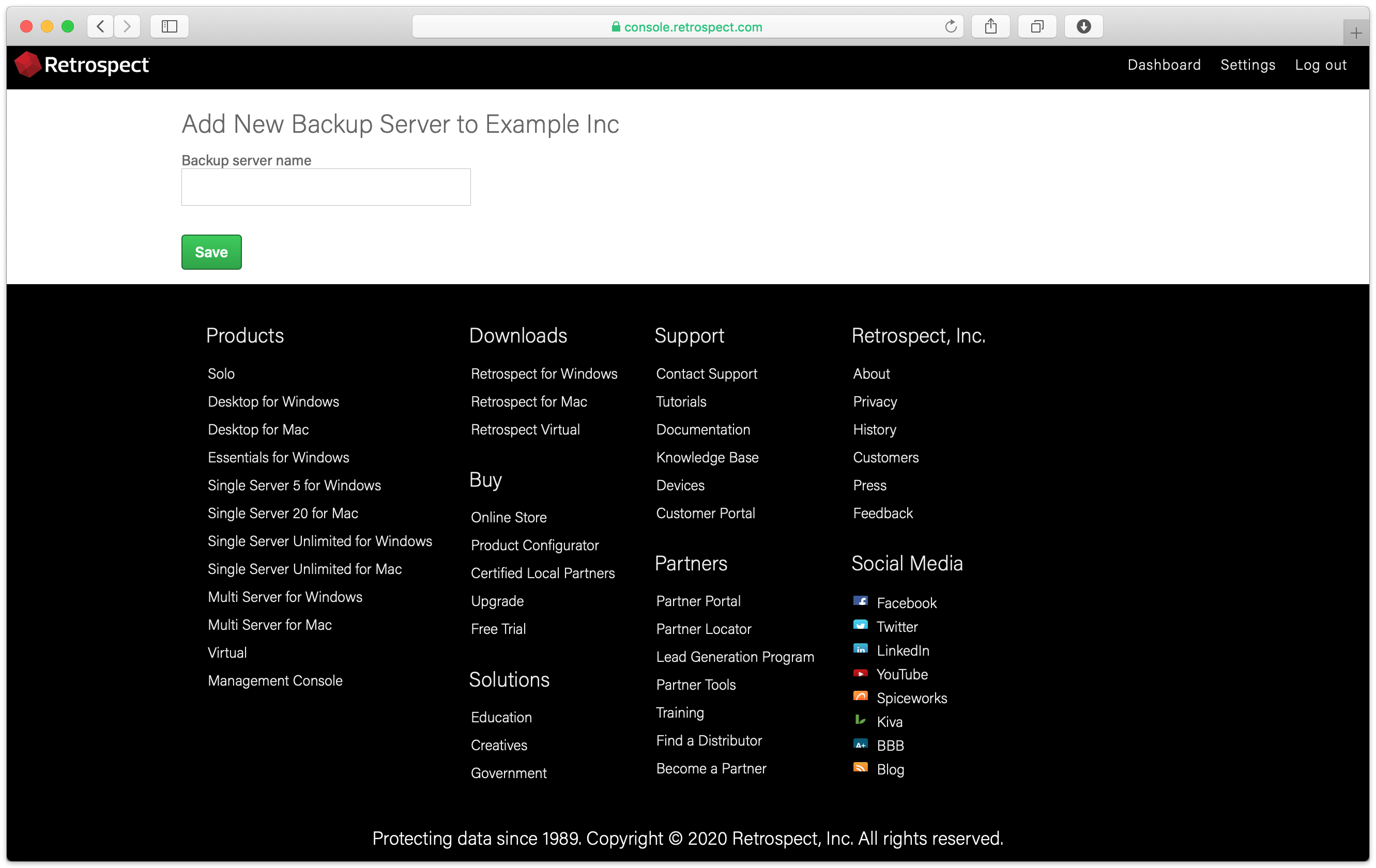
Enter a name for your new backup server.
Click "Add License…", type in your license, and click "Add".
Your custom installer should now be visible. Click "Download".
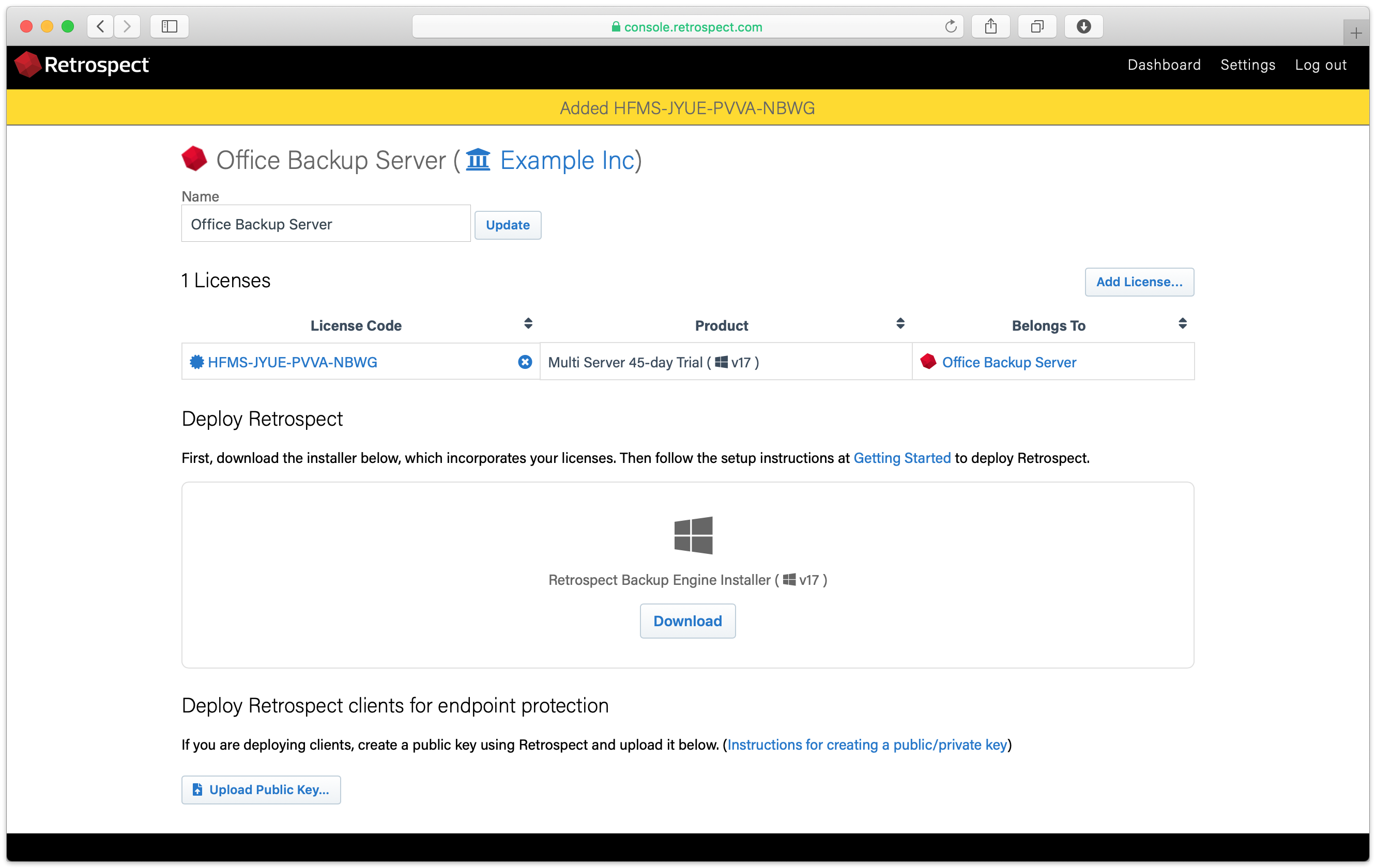
Unzip the download.
For Mac, run "Install Retrospect". At the end, Retrospect will be launched.
For Windows, run "Install Retrospect" and select "Install Retrospect". After it completes, launch Retrospect.
Retrospect is now licensed and connected to Retrospect Management Console under your account.
Deploying a Shared Script
The Retrospect Management Console supports mass deployment of scripts through its Shared Scripts workflow. With Shared Scripts, IT administrators or partners can update a set of Retrospect Backup engines with a common ProactiveAI script to a single cloud destination. See the following step-by-step guide.
Log into your Retrospect Management Console account and click on "Settings" to access your account at the top right of the screen.
Click on "Scripts". You will see a list of Shared Scripts with a summary of each, including deployments.
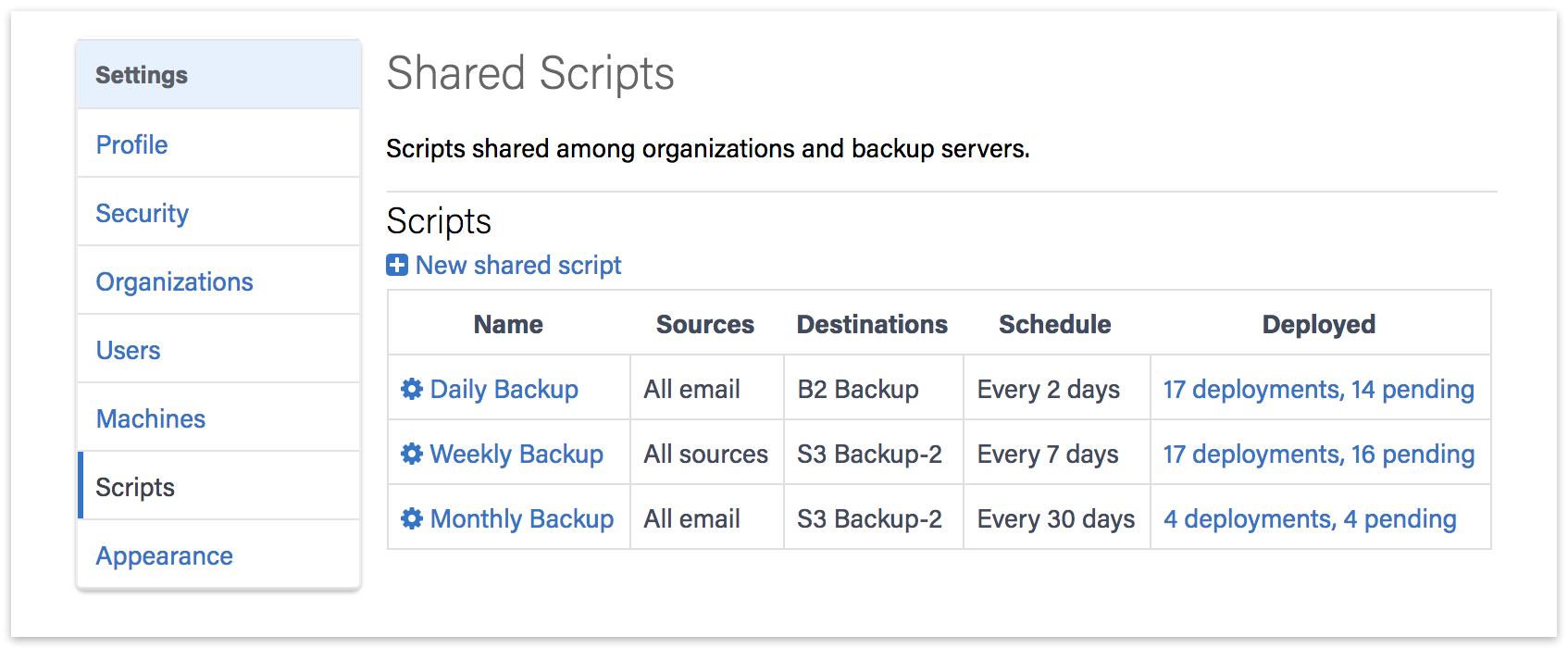
Click on "New Shared Script". You will be able to select which source containers you want to include, which cloud destination, and the schedule.
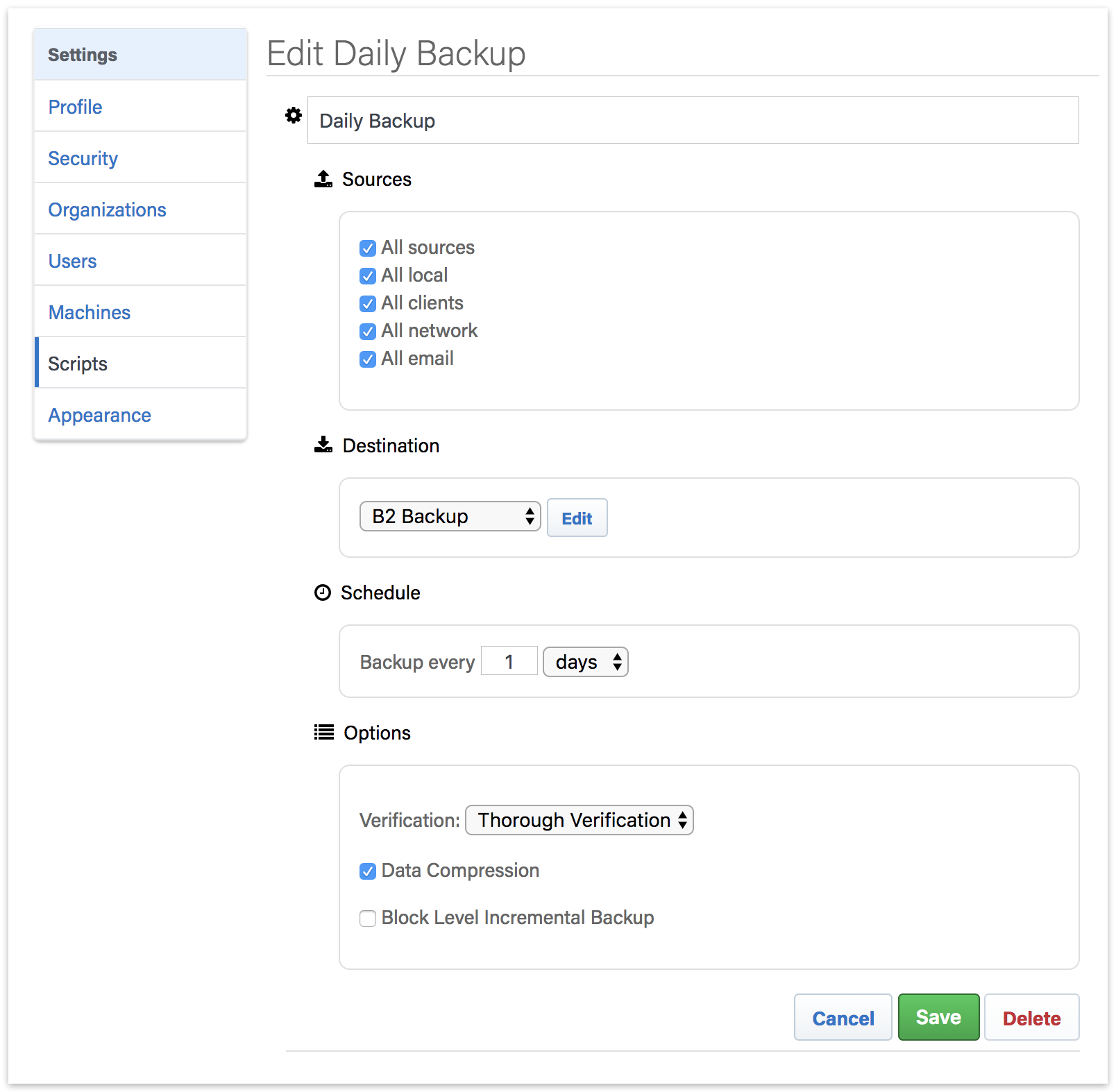
For the "Destination", you can select between Amazon S3 compatible providers and B2. For a B2 cloud destination, enter the bucket name. For an Amazon S3 compatible provider, use the entire URL with bucket name.
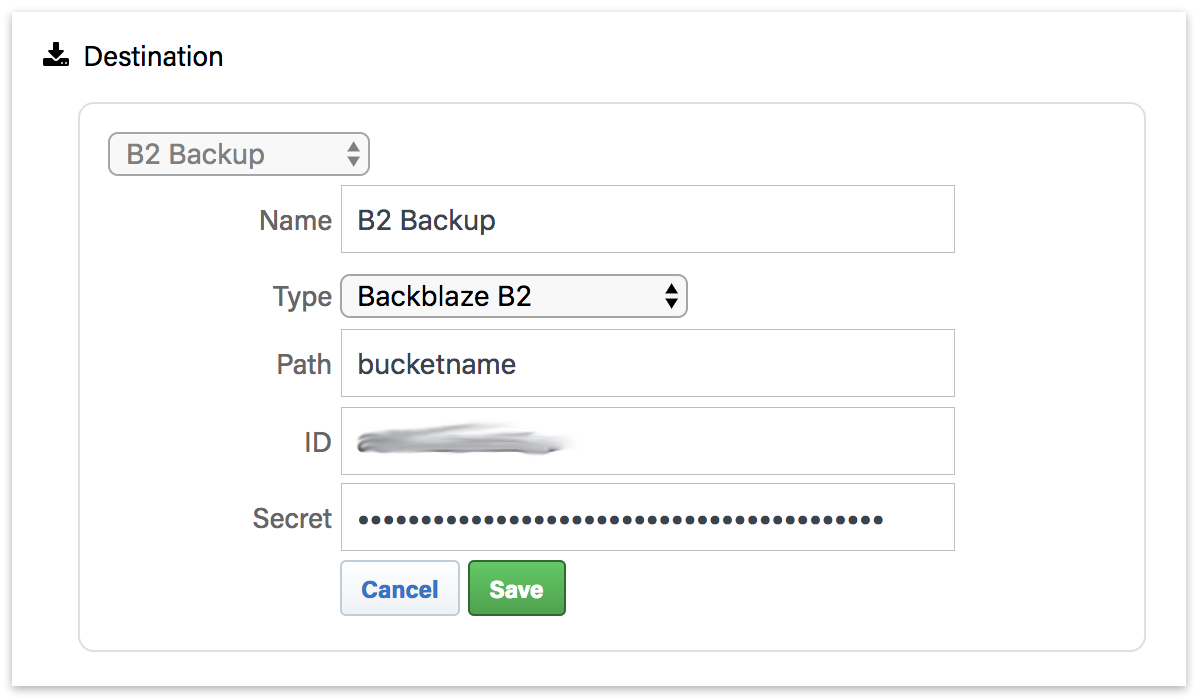
After you save the script, select that script's deployment options. Select the engines that you would like to deploy this Shared Script to and click "Save". The script will then be deployed to those engines.
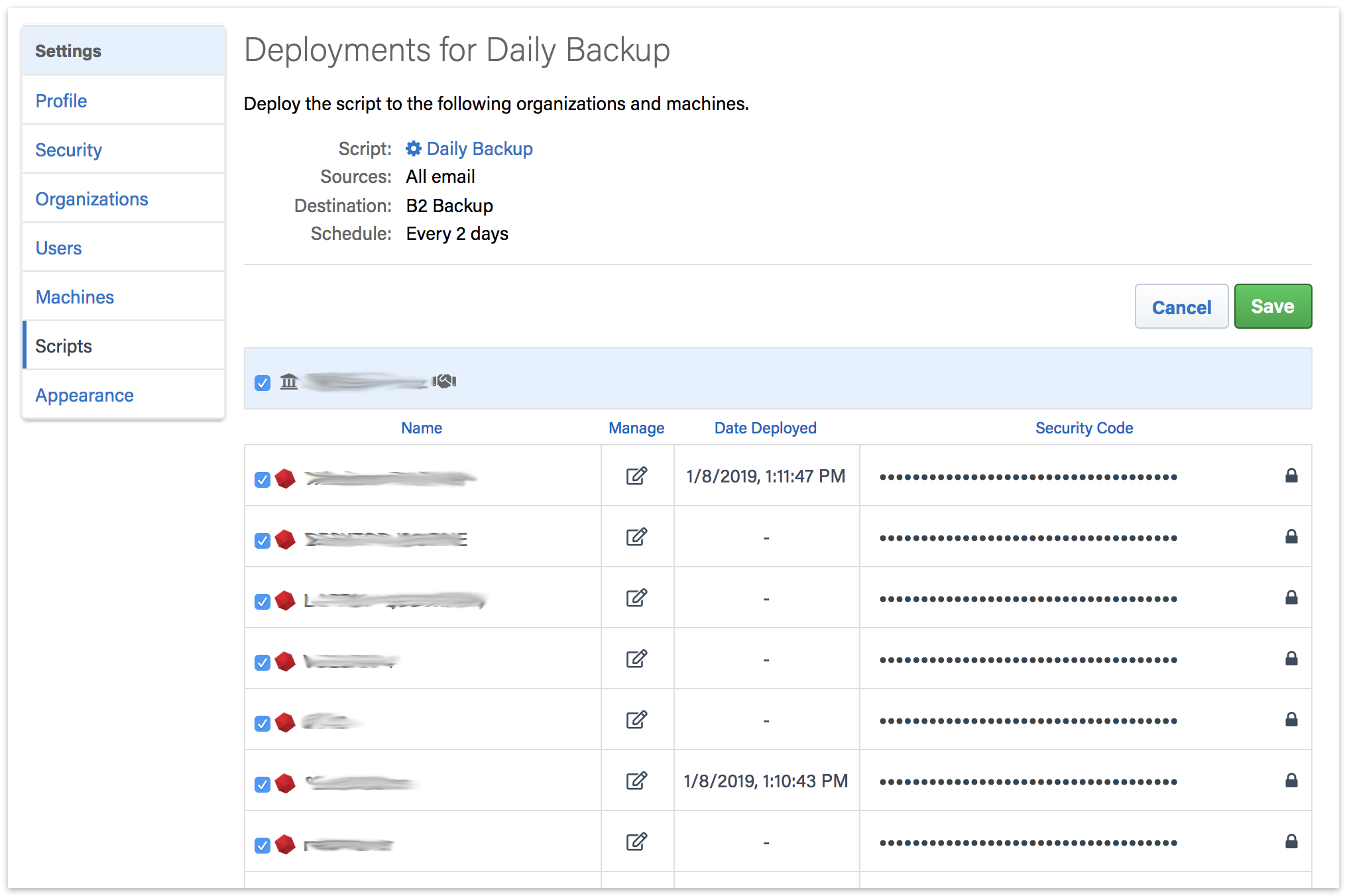
All Shared Scripts are use AES-256 encryption. You will find the encryption key in the "Deployments" tab under "Security Code". Each backup set will be named 'Destination Name-Engine Name' to ensure the separate Storage Groups do not use the same destination path.